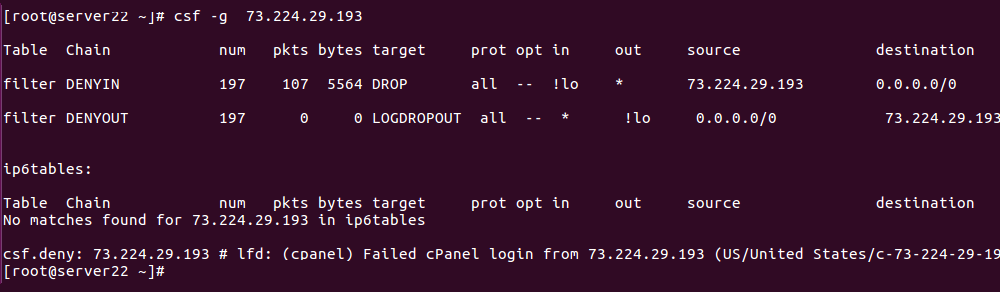
How to list iptables rules
To view all rules in iptables, run Or To list iptables rules without resolving IP to hostname To show the line number To list NAT rules If you run iptables-save command, it will list all iptables rules You can redirect the result of the iptables-save command to a file. You can restore with iptables-restore command. … Read more