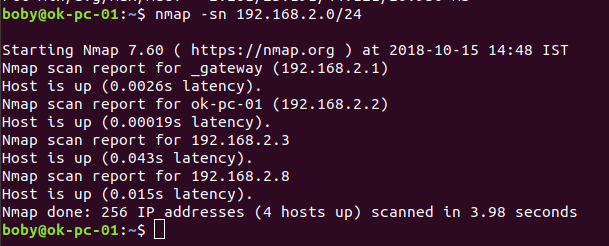
How to find Operating System of a remote computer using nmap?
Nmap is a network exploration and security auditing tool. It can be used to identify hosts and services on a network, as well as security issues. Nmap can be used to scan for vulnerable open ports on systems. To identify Operating System on a remote server or computer, you can use the command sudo nmap … Read more