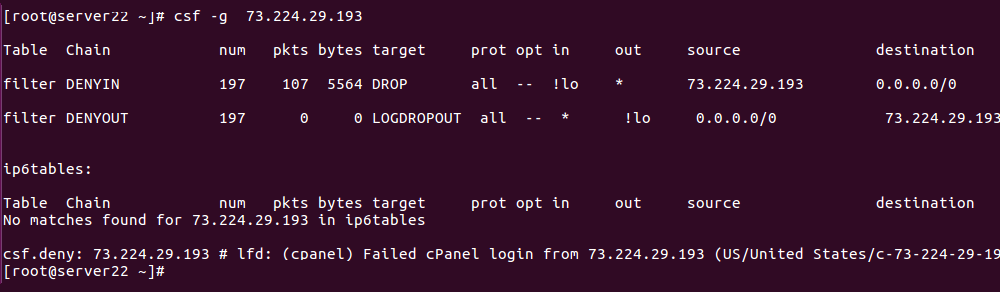
How to whitelist a hostname in CSF firewall
Firewalls usually allow or block IP addresses. If you need to allow a hostname, you need to find the IP address and white list the IP address. If you use dynamic DNS services like noip, dyndns, the IP address of your hostname changes when your internet provider assigns you a new IP address. ConfigServer Security … Read more