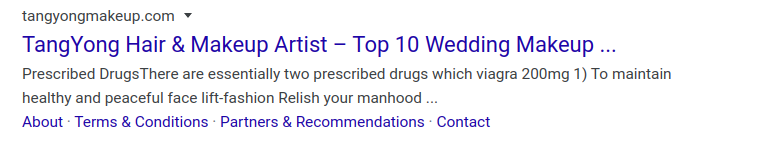
A hacked web site got hacked. The site listed on google SERP with text “There are essentially two prescribed drugs which viagra 200mg”.
When you visit the site in the browser and check the source, you see everything normal, no text related to Viagra. This is because malware on the site only shows that content to Google bot.
To see the malware inserted text, you can use Fetch as Google tool in your Google webmaster center. But before using the fetch as Google tool, you need to verify ownership of the site.
Another way is to change your browsers user agent to same as Google bot
Googlebot/2.1 (+http://www.google.com/bot.html)You can see list of user agents used by google at
https://support.google.com/webmasters/answer/1061943?hl=en
To Fetch as site as google using curl, run
curl --user-agent "Googlebot/2.1 (+http://www.google.com/bot.html)" https://your-site-here.extnBack to curl