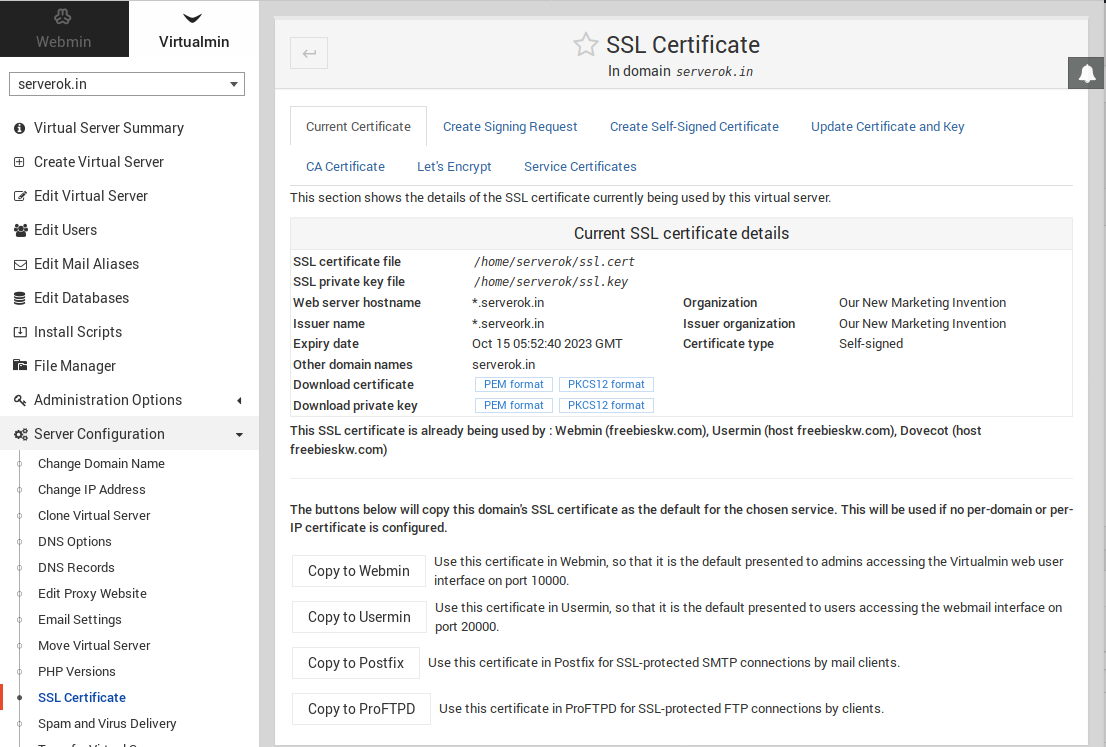
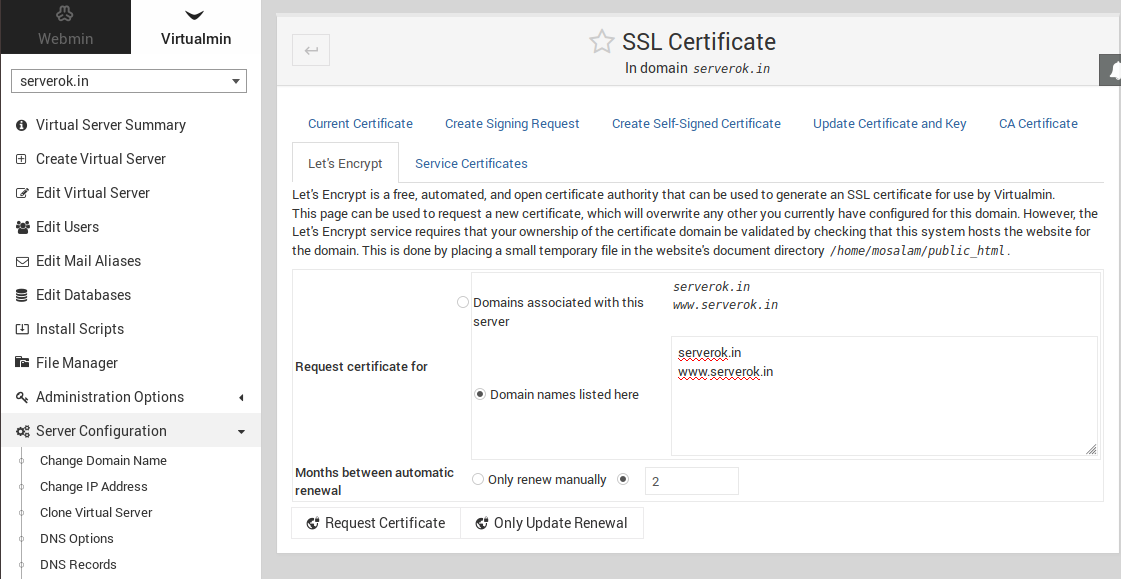
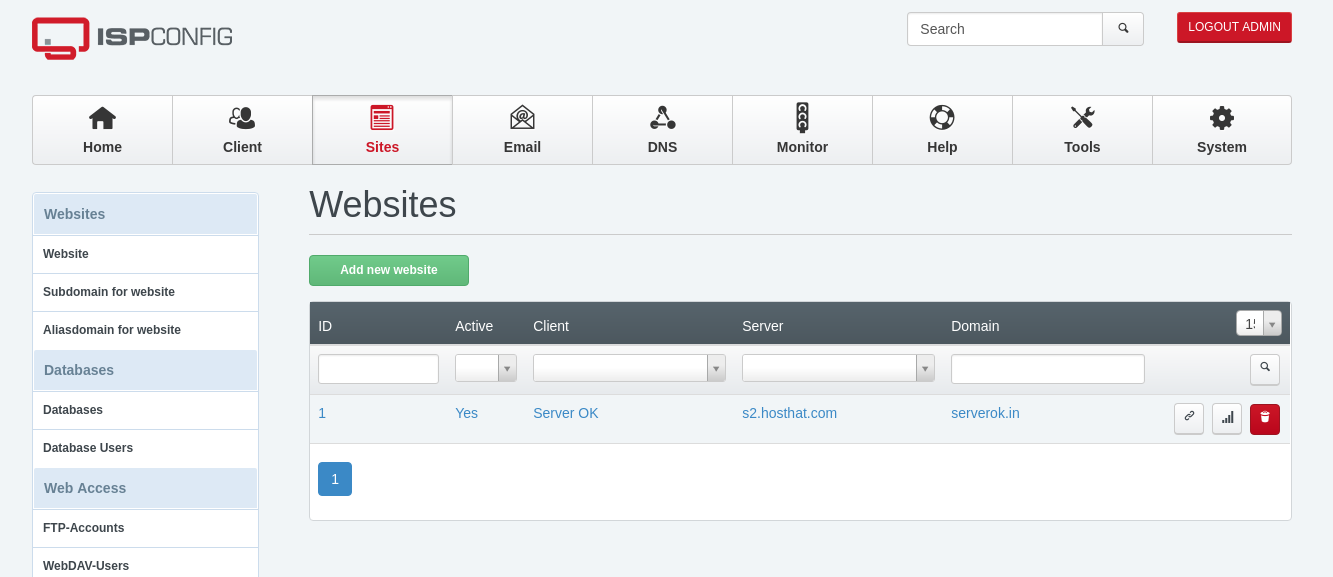
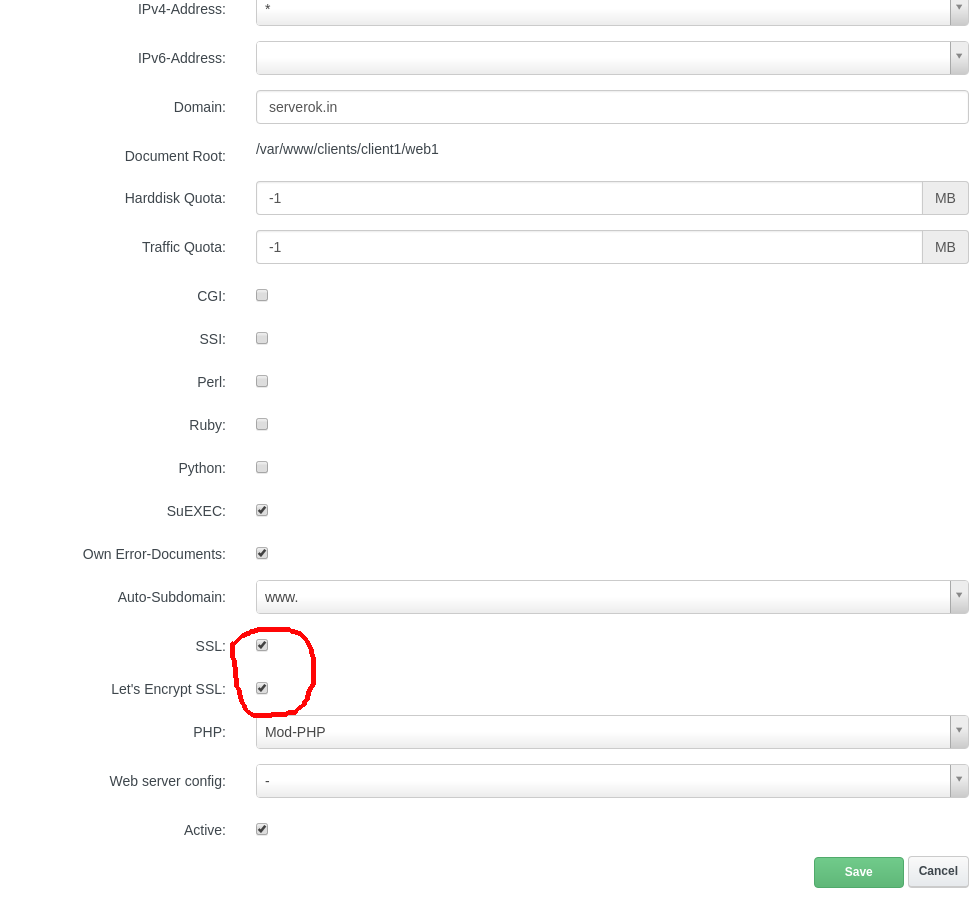
On a server, I have an SSL certificate with 2 domains (doaminA.com and domainB.com)
root@Tombe:~# certbot certificates
Saving debug log to /var/log/letsencrypt/letsencrypt.log
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Found the following certs:
Certificate Name: doaminA.com
Domains: doaminA.com www.doaminA.com domainB.com
Expiry Date: 2022-08-18 11:06:35+00:00 (VALID: 6 days)
Certificate Path: /etc/letsencrypt/live/doaminA.com/fullchain.pem
Private Key Path: /etc/letsencrypt/live/doaminA.com/privkey.pem
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
root@Tombe:~#
domainB.com no longer pointed to this server, so the SSL auto-renewal failed because certbot can’t verify the domain name domainB.com
To fix the problem, run certbot without domainB.com
certbot --cert-name domainA.com -d domainA.com -d www.doaminA.com
This will remove domainB.com from the domainA.com SSL certificate.
Example
root@Tombe:~# certbot --cert-name domainA.com -d domainA.com Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator apache, Installer apache - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - You are updating certificate domainA.com to include new domain(s): (None) You are also removing previously included domain(s): - domainB.com Did you intend to make this change? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (U)pdate cert/(C)ancel: U Renewing an existing certificate
See Letsencrypt