Tor is provided by EPEL repository on CentOS 7. Install EPEL repo with command
yum install epel-release
Install tor
yum install tor
Edit tor config file
vi /etc/tor/torrc
Uncomment or add following lines
HiddenServiceDir /var/lib/tor/hidden_service/ HiddenServicePort 80 127.0.0.1:80
Restart tor with command
systemctl restart tor
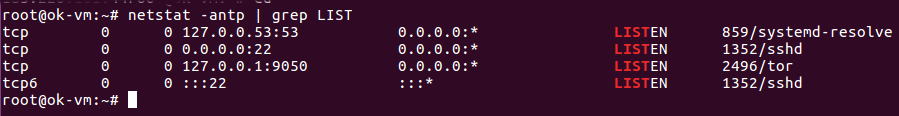
Now your tor hidden service is ready to use. You need to run your web application on 127.0.0.1:80
To see URL of your tor hidden service, run
cat /var/lib/tor/hidden_service/hostname
Make sure to make a backup of folder “/var/lib/tor/hidden_service/” as it comtains keys for this .onion domain. If you lost it, you will lose your domain name. So it is very important you keep the files safe.
To stop/start tor, run
systemctl stop tor systemctl start tor
See tor