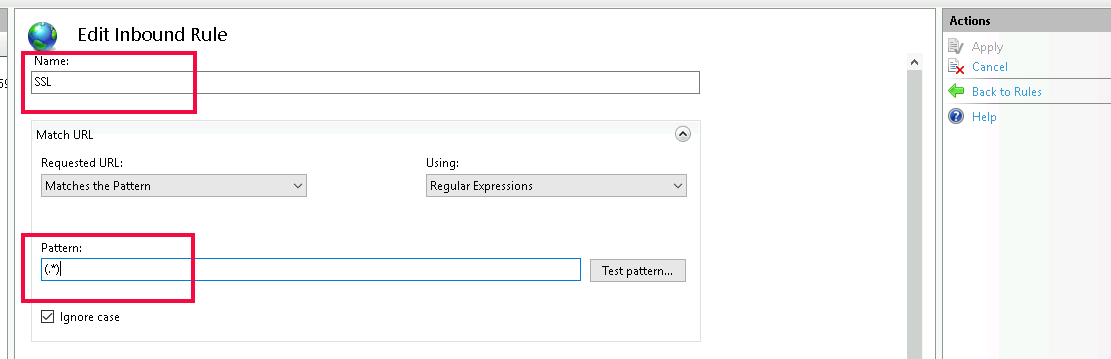
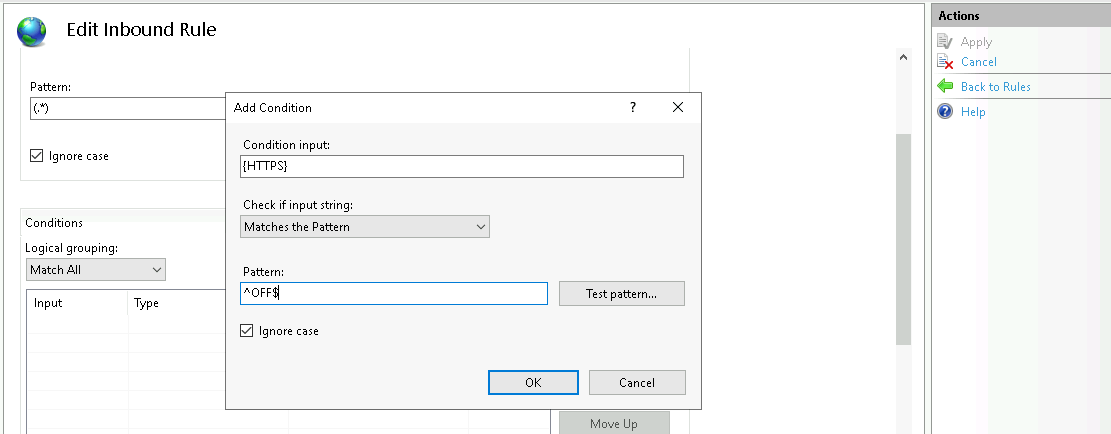
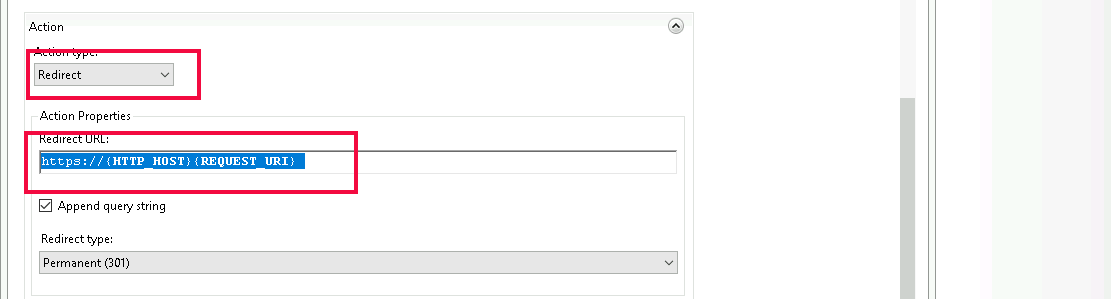
Caddy is a powerful and user-friendly web server. One of its features is its ability to act as a reverse proxy, seamlessly directing client requests to the appropriate backend servers while offering robust security and performance benefits.
To configure caddy as reverse proxy, add following to Caddyfile
vi /etc/caddy/CaddyfileFor reverse proxying to http port, add
rustdesk.serverok.in {
encode gzip
tls admin@serverok.in
reverse_proxy * 100.86.39.125:3000
log {
output file /var/log/caddy/rustdesk.access.log
}
}For proxying to https port:
serverok.in {
reverse_proxy * 10.1.1.1:443 {
transport http {
tls
tls_insecure_skip_verify
}
}
}Restart Caddy
systemctl restart caddyIn this case, all request for domain serverok.in will be proxied to backend server IP address 10.1.1.1 on port 443.
tls_insecure_skip_verify is to specify not to validate backend server SSL certificate to allow self signed SSL certificate.
To enable logging
serverok.in {
reverse_proxy * 10.1.1.1:443 {
transport http {
tls
tls_insecure_skip_verify
}
}
log {
output file /var/log/caddy/serverok.in.access.log
}
}This will save logs in JSON format.
If you need to allow multiple domains, separate them with comma.
serverok.in, www.serverok.in {
reverse_proxy * 10.1.1.1:443 {
transport http {
tls
tls_insecure_skip_verify
}
}
log {
output file /var/log/caddy/serverok.in.access.log
}
}To redirect www domain to non-www
www.serverok.in {
redir https://serverok.in{uri}
}Back to Caddy