Lego is a Let’s Encrypt client and ACME library written in Go.
https://go-acme.github.io/lego
Install Lego
To install go to the release page, download the latest version.
wget https://raw.githubusercontent.com/serverok/server-setup/master/install/lego.sh
bash ./lego.sh
Create SSL certificate
To create an SSL certificate standalone (built-in webserver), run
lego --accept-tos --http --email="EMAIL-ADDRESS" --key-type rsa2048 --domains="DOMAIN_NAME" --domains="www.DOMAIN_NAME" --path="/etc/lego" run
If you need to verify using port 443, use “–tls” instead of “–http”
Verify SSL using webroot (existing webserver)
lego --accept-tos --http --http.webroot="/var/www/html/" --email="EMAIL-ADDRESS" --key-type rsa2048 --domains="DOMAIN_NAME" --domains="www.DOMAIN_NAME" --path="/etc/lego" run
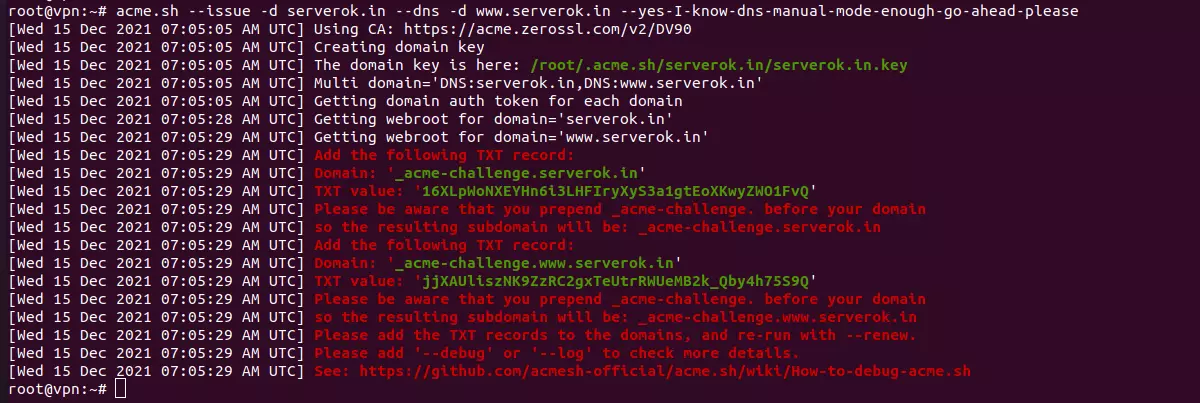
Issue Wildcard SSL using manual DNS verification
lego --email "EMAIL-ADDRESS" --key-type rsa2048 --domains="DOMAIN_NAME" --domains="*.DOMAIN_NAME" --dns "manual" --path="/etc/lego" run
Renew SSL certificate
To renew the SSL certificate, use the same command as SSL creation with “run” replaced with
renew --days 30
–days 30 means SSL will be renewed if the expiry date is with 30 days. If you need to force renew SSL, use –days 90.
Now run
lego --http --http.webroot="/var/www/html/" --email="EMAIL-ADDRESS" --key-type rsa2048 --domains="DOMAIN_NAME" --domains="www.DOMAIN_NAME" --path="/etc/lego" renew --days 30
You need to restart the webserver after running this command.
Renew Hook
If you need to execute a script after SSL renewal, you can add
--renew-hook="./myscript.sh"
Example
lego --http --http.webroot="/var/www/html/" --email="EMAIL-ADDRESS" --key-type rsa2048 --domains="DOMAIN_NAME" --domains="www.DOMAIN_NAME" --path="/etc/lego" renew --days 30 --renew-hook="./myscript.sh"
If you are using the standalone method, you need to stop the webserver before running the lego command.
SSL certificates will be in the directory
/etc/lego/certificates/
Make it readable by the web server with the command
chmod -R 755 /etc/lego/
See letsencrypt